When has the UK faced cyberattacks in the past?
The Independent looks at recent cyber attacks on Microsoft, the British Army and coronavirus researchers

Your support helps us to tell the story
This election is still a dead heat, according to most polls. In a fight with such wafer-thin margins, we need reporters on the ground talking to the people Trump and Harris are courting. Your support allows us to keep sending journalists to the story.
The Independent is trusted by 27 million Americans from across the entire political spectrum every month. Unlike many other quality news outlets, we choose not to lock you out of our reporting and analysis with paywalls. But quality journalism must still be paid for.
Help us keep bring these critical stories to light. Your support makes all the difference.
The massive cyberattack targeting the UK’s Ministry of Defence is the latest in a long line of hacks forming a frontline of modern warfare.
The MoD attack, believed to have been carried out by China, was on a third-party payroll system including the details of tens of thousands of British armed forces and veterans, Sky News reported.
But cabinet minister Mel Stride said the government was not yet pinning the blame on Beijing despite a long history of the West blaming both China and Russia for previous attacks.
He told Sky News: “That is an assumption. Where we are not saying that at this precise moment.”
Here, The Independent looks at other recent cases of government departments, contractors and MPs being hacked.

Electoral Commission - March 2024
China state-affiliated cyber actors were behind the “malicious” targeting of parliamentarians and a cyber attack on the Electoral Commission, the National Cyber Security Centre (NCSC) said back in March.
The UK’s cyber security agency said it believes a China-backed group known as APT31 was responsible for a campaign of online spying against the email accounts of a group of MPs and peers critical of China.
When the attack was made public it was confirmed the hackers had been able to access reference copies of the electoral registers, held by the commission for research purposes and to enable permissibility checks on political donations.
The registers held at the time of the cyber attack include the name and address of anyone in the UK who was registered to vote between 2014 and 2022, as well as the names of those registered as overseas voters.
The Electoral Commission said the attack “did not have an impact on the security of UK elections, and resilience has been strengthened since the attack”.
Star Blizzard - December 2023
Russia’s intelligence services targeted high-profile British politicians, civil servants and journalists with cyberespionage and “malicious cyberactivity” as part of sustained attempts to interfere in political processes.
The Foreign Office said Russia’s FSB agency was responsible for a range of cyberespionage operations including targeting British parliamentarians from multiple parties from at least 2015 and selectively leaking and amplifying sensitive information to serve Russian interests.
Foreign Office minister Leo Docherty told lawmakers that a cybergroup known as “Star Blizzard” or Callisto Group, which British cybersecurity officials believe to be “almost certainly subordinate” to an FSB unit, created false identities to impersonate legitimate contacts and then delivered malicious links to victims.
Army hacked to promote NFTs - July 2022
The British Army confirmed a “breach” of its Twitter and YouTube accounts when the channel featured videos promoting cyptocurrency and images of billionaire businessman Elon Musk.
The official Twitter account had retweeted a number of posts appearing to relate to NFTs (non-fungible tokens).
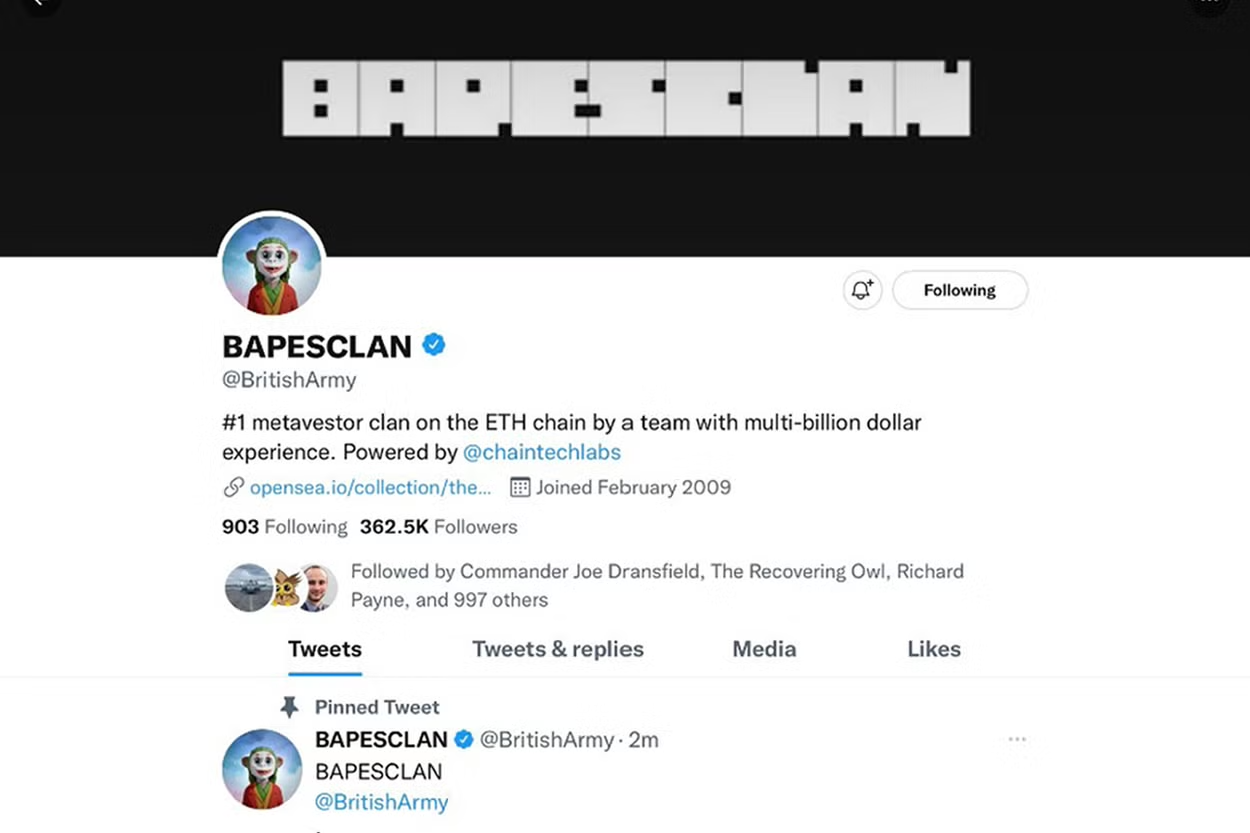
At one stage, the account name was changed to Bapesclan and the profile picture was an ape-like cartoon figure in clownish make-up.
A tweet posted afterwards read: “Apologies for the temporary interruption to our feed. We will conduct a full investigation and learn from this incident. Thanks for following us and normal service will now resume.”
Microsoft Exchange - July 2021
Britain previously accused China of carrying out “systematic cyber sabotage” after an attack on Microsoft Exchange email services affected a quarter of a million servers worldwide.
US and other Nato member states, the European Union, Australia, New Zealand and Japan decided to pool resources after accusing China of being behind criminal hacking groups who targeted Microsoft Exchange servers in early 2021.
The state-sponsored blackmail means that the Chinese government is complicit in demanding millions of dollars from private companies in exchange for digital keys that allow victims to regain access to their computer networks, say western security officials.
Their wide-ranging and expanding activities include not just espionage, but extortion by spreading ransomware and cryptojacking.

SolarWinds hack April 2021
Britain accused Russia’s foreign intelligence service of being behind what is believed to be one of the most serious cyber espionage attacks to have faced the US.
The National Cyber Security Centre (NCSC) had assessed that it was “highly likely” Moscow was behind the SolarWinds hack, which saw hackers infiltrate government agencies and corporate secrets of the likes of Microsoft in early 2020.
Russian hackers are believed to have infected the IT service firm’s widely used Orion software with a malicious code enabling them to access the systems of at least nine US agencies and 18,000 organisations worldwide, including Nato and the European Parliament.
The impact of the hack in the UK was assessed to be “low”, according to the findings of the National Cyber Security Centre (NCSC) shared by the FCDO, with a “low single digit number” of public sector bodies having been targeted.
Coronavirus - July 2020
Britain, the United States and Canada all accused Russian spies of targeting scientists seeking to develop a coronavirus vaccine.
The three allies said hackers linked to Russian intelligence were seeking to steal the secrets of research bodies around the world, including in the UK.
In a coordinated announcement with security agencies in the US and Canada, the NCSC pointed the finger at an established hacker group known as APT29, Cozy Bear or The Dukes.
It is believed that vaccine research facilities at Oxford University and Imperial College London are among the institutions targeted by the hackers, who are thought to operate by exploiting weaknesses in VPN and external mail services used by researchers.
Subscribe to Independent Premium to bookmark this article
Want to bookmark your favourite articles and stories to read or reference later? Start your Independent Premium subscription today.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments