Bad Rabbit: Fresh ransomware spreads across Europe after WannaCry and Petya outbreaks
'Based on our investigation, this is a targeted attack against corporate networks'
A new cyber attack is affecting computer systems around Europe.
A strain of ransomware known as "Bad Rabbit" is believed to be behind the trouble, and has spread to Russia, Ukraine, Turkey and Germany.
Cyber security firm Kaspersky Lab, which is monitoring the malware, has compared it to the WannaCry and Petya attacks that caused so much chaos earlier this year.
According to the company, the majority of victims are located in Russia, and the ransomware appears to have infected devices through the hacked websites of Russian media organisations.
Interfax and Fontanka in Russia have both been hit by a cyber attack, as have Odessa Airport and the Kiev Metro in Ukraine.
"Based on our investigation, this is a targeted attack against corporate networks, using methods similar to those used in the ExPetr attack," Kaspersky Lab has said. "However, we cannot confirm it is related to ExPetr."
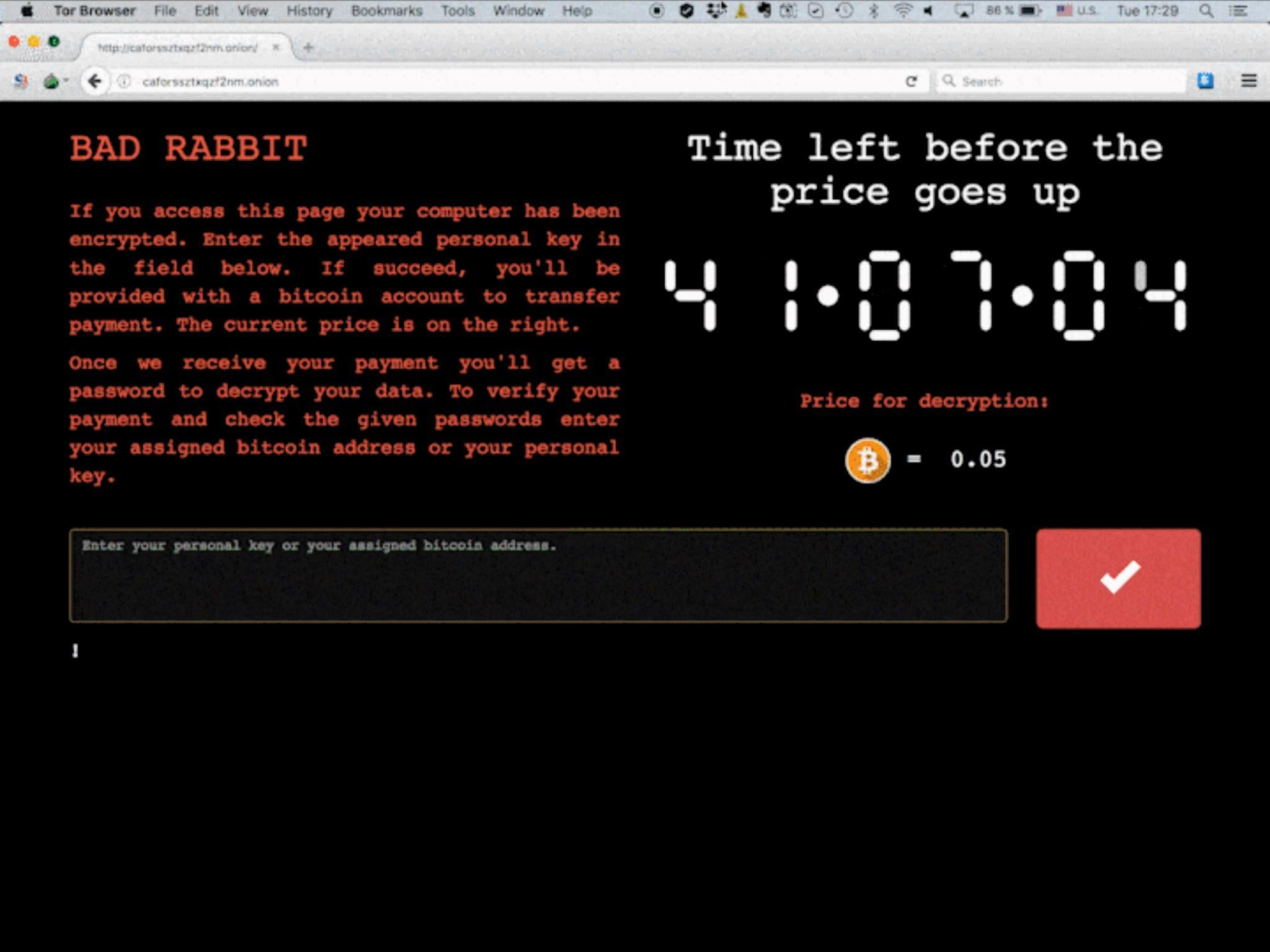
The cyber criminals behind Bad Rabbit are locking computers down and demanding 0.05 Bitcoin (£220) from victims, in exchange for the restoration of their devices.
However, security experts always advise people against paying the ransom. This is because it encourages more attacks, and there's no guarantee the attackers will actually honour their word and remove the malware from your device.
According to the Bad Rabbit ransom screen, the fee will rise in the near future.
Ukraine’s cyber police chief has told Reuters that the country was “barely affected”.
In May, the “WannaCry” ransomware attack forced hospitals, factories and businesses around the world to shut down because they could not access critical computer systems.
Additional reporting by Reuters
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments
Bookmark popover
Removed from bookmarks