The Independent's journalism is supported by our readers. When you purchase through links on our site, we may earn commission.
Imperceptible internet scam to trick Google Chrome users to visit dodgy websites returns
The attack exploits the fact that lots of different characters look identical
People are being warned about an old phishing technique capable of duping even the most clued-up internet users.
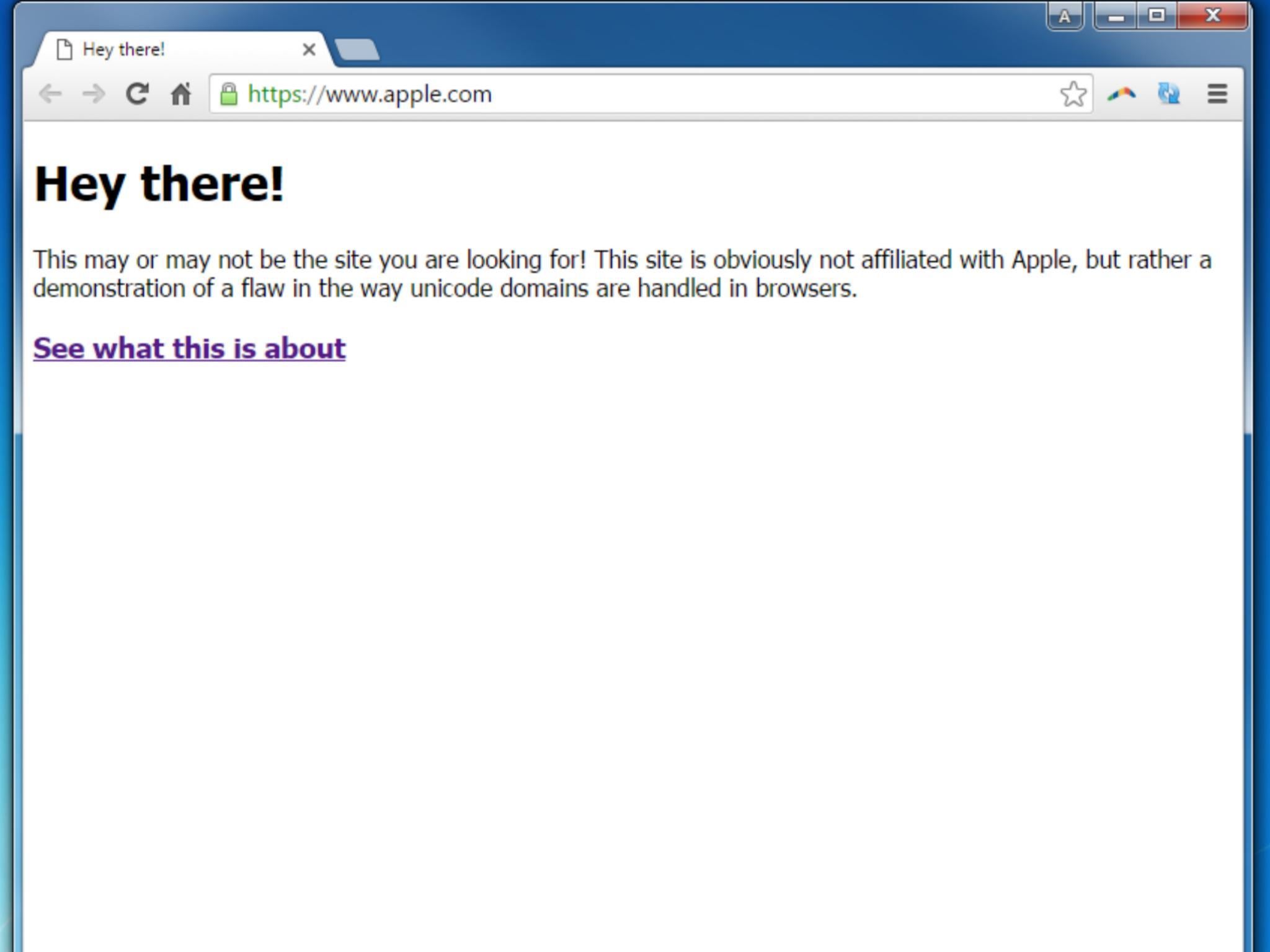
Web developer Xudong Zheng recently created a fake version of apple.com, which appears to have the exact same URL as the iPhone-maker’s online store.
Most people would have no issue clicking on the link, which appears to be completely legitimate. However, its actual URL is: “xn—80ak6aa92e.com”.
There’s no malicious intent behind Mr Zheng’s fake apple.com, which simply contains a message reading, “Hey there! This may or may not be the site you are looking for! This site is obviously not affiliated with Apple, but rather a demonstration of a flaw in the way unicode domains are handled in browsers.”
Cyber criminals, though, can use the same technique to trick users into visiting infected websites.
It’s an old scam, known as an internationalised domain name (IDN) homograph attack, which was first reported back in 2001.
The attack exploits the fact that lots of different characters look the same, and sneakily replaces certain Latin characters with identical- or near-identical-looking characters from non-Latin alphabets, such as Cyrillic.
The URL for Mr Zheng’s fake Apple website uses a Cyrillic ‘a’, which is impossible to distinguish from the ASCII ‘a’. ASCII is an encoding standard for characters familiar to English readers, a hangover from the internet’s early days as a US creation.
However, potential scammers can use a tool called Punycode to translate characters from Unicode, an encoding standard for a much wider range of characters, into ASCII, transforming a URL most internet users would never click on to something that looks completely innocent.
Chrome 58, which was released this week, protects users from the issue. People using older versions of Google’s popular browser can still be affected, so it’s important to update.
The scam also works on Firefox, but not Safari or Internet Explorer.
Firefox users can protect themselves by typing about:config into the address bar and marking network.IDN_show_punycode as True. This will display IDN domains in their Punycode form.
Mr Zheng says concerned users can also take extra precautions by manually typing out URL or navigating to sites via a search engine.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments
Bookmark popover
Removed from bookmarks