Mystery of fake US mobile phone towers capable of tapping smartphones
No-one knows who operates the towers - or why

Fake mobile phone towers dotted across America could be listening in on unsuspecting citizens by tapping their smartphones, according to new reports.
The decoy towers are known as ‘interceptors’ and although their operators are anonymous, it’s known that similar technology is used by both US military and local police forces.
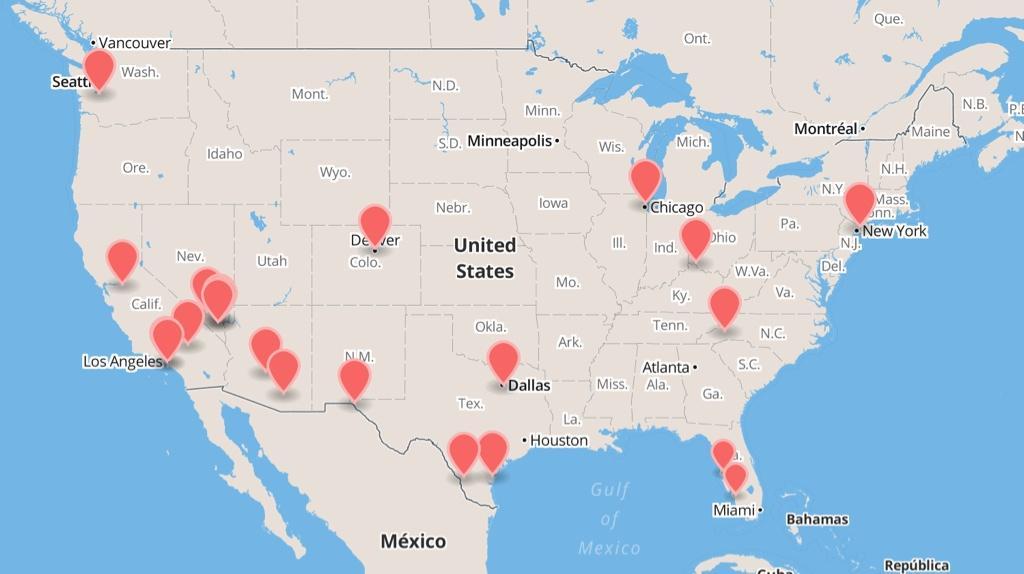
Seventeen of these towers were discovered in a month by security firm ESD America while they were testing their ultra-secure smartphone: a heavily customized Android device that is built into a Samsung Galaxy S3 body and sells for $3,500.
“Interceptor use in the U.S. is much higher than people had anticipated,” ESD America CEO Les Goldsmith told Popular Science. “One of our customers took a road trip from Florida to North Carolina and he found 8 different interceptors on that trip.”
Goldsmith adds that the interceptors are often found “right on top” of military bases. “So we begin to wonder – are some of them U.S. government interceptors? Or are some of them Chinese interceptors? Whose interceptor is it? Who are they, that's listening to calls around military bases?"
Interceptor technology varies in sophistication but all use a method of infiltration known as ‘baseband attack’ – essentially bypassing the consumer-focused apps and software (eg iOS and Android) to 'talk' to the most basic parts of a smartphone that exchange data with mobile towers.
It’s thought that US security agencies use baseband attacks for a number of reasons, with documents leaked by Edward Snowden suggesting that the NSA has the capacity to use these ‘over-the-air’ methods to activate a device’s microphone even when it’s powered down.
These types of attack are also the forte of ‘stingray’ devices used by both local and state law enforcement. A report by Ars Technica last month found that the FCC was currently investigating the “illicit and unauthorized use” of these – though it’s not clear whether this will cover interceptor towers as well.
The American Civil Liberties Union (ACLU) has previously found that 15 states used stingray equipment to snoop on mobile devices, with many of these – including California, Arizona, Texas, Florida and New York – also playing host to interceptor towers in ESD’s report.
For the moment though it’s unclear just who is using these devices and why. As Mr Goldmsith concluded: “The point is: we don't really know whose they are."
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments
Bookmark popover
Removed from bookmarks